Startup, Entrepreneurship and Certification. You will also find the trending articles
Labels
- 000
- 000 Web Designer Guide: A Practical Guide for Wealth and Freedom for Freelancer
- 3 Axis Drone Gimbal
- 30Seconds
- 55165A-Excel2016
- ACCA
- Action
- Adobe
- Adventure
- ai
- AI Ethics Complete Guide 2021 with Assessment Questions
- Alphabet The Letter H
- Alphabet The Letter I
- Alphabet The Letter J
- Alphabet The Letter K
- Alphabet The Letter L
- Alphabet The Letter m
- Animation
- appdesign
- Audio Book How to Talk to Anyone 92 Little Tricks for Big Success in Relationships & Business
- Audio Book Secret to Achieving All Your Goals: An Advanced Course in Personal Achievement
- BA
- Become Product Manager
- BEST BUSINESS SCHOOLS in USA 2021-2022 by Bloomberg Businessweek
- BI
- Biography
- Bollywood
- Business
- Business Analysis
- Business Analyst
- Business Intelligence
- Cars
- CCNA
- Cloud Gaming
- Comdy
- Corona-COVID19
- Crime
- Cybersecurity
- designing
- designthinking
- Developing IoT Projects with ESP32
- digitaldesign
- Drama
- Entertainment
- Entrepreneurs
- Fit Foods and Fakeaways 100 Healthy and Delicious Recipes Book - Courtney Black
- Games
- Gujranwala
- Hollyood
- Hollywood
- How to
- Javascript
- Kids
- kidscartoon
- KPI
- Lollywood
- MCSE
- Microsdoft
- Movies
- Music
- Mystery
- Network Engineer
- Object Oriented Programming
- PMP
- Pre-Activated
- Product Management
- Product Management Course
- Project Management
- Romance
- Sci-Fi
- SEO
- Software
- Software Engineering
- Sports
- Startup
- System Engineer
- Taylor Swift
- Technology
- The $1
- Thriller
- Trending
- ui/ux
- Windows
- Windows 11
- Windows 7
- Youtube
- YouTube CEO
Recent
Popular
-
There is a limit to number of times activation of Windows 7 can be made online automatically, even though the product key been used to ac...
-
How to make Count Down Timer in PowerPoint In this video we will learn the best practices for Power Point the most demanding skill of ...
-
How to make Count Down Timer in PowerPoint In this video we will learn the best practices for Microsoft Excel the most demanding skill...
Labels
- 000 (1)
- 000 Web Designer Guide: A Practical Guide for Wealth and Freedom for Freelancer (1)
- 3 Axis Drone Gimbal (1)
- 30Seconds (1)
- 55165A-Excel2016 (3)
- ACCA (9)
- Action (5)
- Adobe (8)
- Adventure (3)
- ai (2)
- AI Ethics Complete Guide 2021 with Assessment Questions (1)
- Alphabet The Letter H (1)
- Alphabet The Letter I (1)
- Alphabet The Letter J (1)
- Alphabet The Letter K (1)
- Alphabet The Letter L (1)
- Alphabet The Letter m (1)
- Animation (3)
- appdesign (1)
- Audio Book How to Talk to Anyone 92 Little Tricks for Big Success in Relationships & Business (1)
- Audio Book Secret to Achieving All Your Goals: An Advanced Course in Personal Achievement (1)
- BA (37)
- Become Product Manager (2)
- BEST BUSINESS SCHOOLS in USA 2021-2022 by Bloomberg Businessweek (1)
- BI (7)
- Biography (1)
- Bollywood (5)
- Business (1)
- Business Analysis (20)
- Business Analyst (39)
- Business Intelligence (34)
- Cars (1)
- CCNA (20)
- Cloud Gaming (1)
- Comdy (2)
- Corona-COVID19 (7)
- Crime (1)
- Cybersecurity (1)
- designing (1)
- designthinking (1)
- Developing IoT Projects with ESP32 (1)
- digitaldesign (1)
- Drama (9)
- Entertainment (1)
- Entrepreneurs (14)
- Fit Foods and Fakeaways 100 Healthy and Delicious Recipes Book - Courtney Black (1)
- Games (1)
- Gujranwala (3)
- Hollyood (1)
- Hollywood (36)
- How to (26)
- Javascript (1)
- Kids (12)
- kidscartoon (13)
- KPI (3)
- Lollywood (1)
- MCSE (2)
- Microsdoft (3)
- Movies (17)
- Music (1)
- Mystery (3)
- Network Engineer (9)
- Object Oriented Programming (1)
- PMP (3)
- Pre-Activated (1)
- Product Management (2)
- Product Management Course (2)
- Project Management (4)
- Romance (2)
- Sci-Fi (1)
- SEO (1)
- Software (2)
- Software Engineering (3)
- Sports (1)
- Startup (3)
- System Engineer (2)
- Taylor Swift (1)
- Technology (13)
- The $1 (1)
- Thriller (6)
- Trending (5)
- ui/ux (18)
- Windows (5)
- Windows 11 (1)
- Windows 7 (12)
- Youtube (1)
- YouTube CEO (1)
Featured Post
Is Business Analyst fill the Gap?
Is Business Analyst fill the Gap? Bridging the Gap: How Business Analysts Fill Crucial Business Gaps In today's fast-paced and ever-cha...
Technology
Latest Post
How to check Windows is Genuine / Activated ?
How to Confirm that the Windows 8 System is Activated Successfully
After installing and activating the Windows 8 system, many users find
that the system shows successful activation, but not really activated
when in real use.
Here, a simple method for checking if the Windows 8 system is activated successfully:
1. Hold down the "Win+F" on the keyboard into the search dialog box.
2. Enter "cmd" in the dialog box and press Enter on the keyboard.

2. In the new pop-up dialog box, enter "slmgr/xpr".

3.
Check the new pop-up dialog box. If Windows 8 is successfully
activated, software version information and the expiration date will be
displayed.

How to build a CISCO network in home
How to build a CISCO network in home
If you are used to working with home networking gear, you will be used to an integrated device that “does it all”. On a home network, you may have one box that is a cable/DSL modem, router, firewall, switch, and wireless access point all in one. It is amazing all the functions they can fit into one box.
If you are studying Cisco networking and learning about how businesses use these devices, you may be wondering why there is so much importance on the differences between a switch, router, firewall, and other network devices. If the home user can have all these devices combined into one, why doesn’t the business user do this as well? So, now, here we try to find out what the main differences between these network devices.
Integrated devices
Just like home devices, business devices have become more and more consolidated over time but not to the extent that the home devices have. Network administrators in a business network are more comfortable having separate devices and even like the idea. This is because network administrators like to be able to isolate problems down to a certain device and they like to be able to know the performance capabilities of every device. If you use an integrated router, switch, and firewall all into one device, troubleshooting, managing, and understanding the performance capabilities of that device gets complicated. I’m not saying that this isn’t done. You can buy a big & expensive, chassis-based, Cisco 6500 series switch and have almost all these functions on different blades of the switch. This may be fine for a larger business with a group of administrators but to a medium size business and a single network administrator, many times, this is a scary thought.
Just like home devices, business devices have become more and more consolidated over time but not to the extent that the home devices have. Network administrators in a business network are more comfortable having separate devices and even like the idea. This is because network administrators like to be able to isolate problems down to a certain device and they like to be able to know the performance capabilities of every device. If you use an integrated router, switch, and firewall all into one device, troubleshooting, managing, and understanding the performance capabilities of that device gets complicated. I’m not saying that this isn’t done. You can buy a big & expensive, chassis-based, Cisco 6500 series switch and have almost all these functions on different blades of the switch. This may be fine for a larger business with a group of administrators but to a medium size business and a single network administrator, many times, this is a scary thought.
Keep in mind that for a medium or large size business, these integrated home devices won’t work because they don’t offer all the features required. The standalone routers, switches, and firewalls have many more features than these integrated devices do.
But what is the difference between these devices anyway? Let’s cover the three most popular devices.
Router
A router is a hardware device and has the function of routing packets between networks. A router works at Layer 3 of the OSI model – the Network Layer. This is the layer that the IP protocol works at. Most routers today are IP routers that examine the source and destination IP addresses of each packet, look up the destination of the packet in the router’s IP routing table, and route that packet on its way. In the event that the destination is not listed in the routing table, the router will either send the packet to a default router (if it has one) or drop the packet. Routers are usually used to connect a local area network to a wide-area network (a LAN to a WAN) but can also be used to segment large local area networks (LAN’s).
A router is a hardware device and has the function of routing packets between networks. A router works at Layer 3 of the OSI model – the Network Layer. This is the layer that the IP protocol works at. Most routers today are IP routers that examine the source and destination IP addresses of each packet, look up the destination of the packet in the router’s IP routing table, and route that packet on its way. In the event that the destination is not listed in the routing table, the router will either send the packet to a default router (if it has one) or drop the packet. Routers are usually used to connect a local area network to a wide-area network (a LAN to a WAN) but can also be used to segment large local area networks (LAN’s).
Routers prevent broadcasts. Another way of saying this is that routers form a broadcast domain. So, if your network is being deluged by IP broadcasts, you need to subnet your network into two or more smaller networks. Those networks would be connected by a router and that router wouldn’t allow broadcast traffic to flow between subnets.
Routers use routing dynamic protocols like OSPF, RIP, or BGP to learn routes from other routers. Router can also use static routes that are entered by the administrator.
Routers replace the Ethernet MAC address of the source device with their own MAC address when they send a packet out an interface. When the response to that packet comes back, the new source of the packet is sending the response to the destination of the router. The router receives this, replaces the source address, changes the destination address to the original address, and sends the packet back to the original sender. This is a complex topic that we could spend a whole article covering so this is only meant to provide the most basic understanding of how this works.
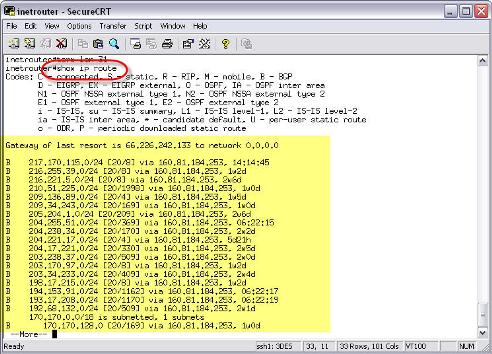
To show the routing table on the router, use the show ip route command. Here is an example of what a routing table looks like on a router:
Switch
A switch is a hardware device that works at Layer 2 of the OSI model – data link. The data link layer is where the Ethernet protocol works.
A switch is a hardware device that works at Layer 2 of the OSI model – data link. The data link layer is where the Ethernet protocol works.
A switch switches Ethernet frames by keeping a table of what MAC addresses have been seen on what switch port. The switch uses this table to determine where to send all future frames that it receives. In Cisco terminology, this table is called the CAM table (content addressable memory). In general, the proper term for this table is the bridge forwarding table. If a switch receives a frame with a destination MAC address that it does not have in its table, it floods that frame to all switch ports. When it receives a response, it puts that MAC address in the table so that it won’t have to flood next time.
A switch is a high-speed multiport bridge. This is why bridges are no longer needed or manufactured. Switches do what bridges did faster and cheaper. Most routers can also function as bridges.
You might be asking how a hub fits into this mix of devices. A hub is a multiport repeater. In other words, anything that comes in one port of a hub is duplicated and sent out all other ports of the hub that have devices attached. There is no intelligence to how a hub functions. A switch is a vast improvement over a hub in terms of intelligence, for many reasons. The most important of those reasons is how the bridge forwarding table works. Intelligent (smart) switches have made hubs obsolete because they can do more at the same cost of a dumb hub. For this reason, hubs are rarely used or sold any longer.
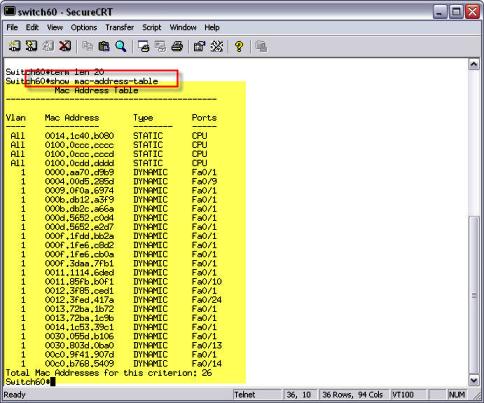
To see this bridge forwarding table (CAM table) on a Cisco switch just type: show mac-address-table
Here is an example:
Firewall
A firewall is used to protect more secure network from a less secure network. Generally, firewalls are used to protect your internal/private LAN from the Internet.
A firewall is used to protect more secure network from a less secure network. Generally, firewalls are used to protect your internal/private LAN from the Internet.
A firewall generally works at layer 3 and 4 of the OSI model. Layer 3 is the Network Layer where IP works and Layer 4 is the Transport Layer, where TCP and UDP function. Many firewalls today have advanced up the OSI layers and can even understand Layer 7 – the Application Layer.
There are a variety of different types of firewalls and we won’t go into that in this article so let’s just talk about the most popular type of firewall – a stateful packet inspection (SPI) hardware firewall. An example of a SPI hardware firewall is a Cisco PIX firewall. This is a dedicated appliance and it looks a lot like a Cisco router.
A SPI firewall is stateful because it understands the different states of the TCP (transmission control protocol) protocol. It knows what is coming and what it going and keeps track of it all. Thus, if a packet tried to come in but it wasn’t requested, the firewall knows that and drops it.
What we have learned about the Network Hardware’s Difference: Integrated Devices, Router, Network Switch & Firewall:
• Routers work at Layer 3 and route IP packets between networks.
• Routers are used to connect a LAN to a WAN (such as your small network to the Internet) but they can also be used to connect segments of a large LAN that has been subnetted into smaller segments.
• Routers route packets based on information in the IP routing table. You can see this table with the show ip route command on a Cisco router.
• Switches work at Layer 2 and switch Ethernet frames. Switches connect multiple devices on a local area network (LAN).
• Switches keep a table of Ethernet MAC addresses called a CAM Table or a Bridge forwarding table. You can see this table with the show mac-address-table command on a Cisco switch.
• Firewalls work at Layers 3 and 4 but some can also work at higher layers.
• Most firewalls can keep track of the states of TCP to prevent unwanted traffic from the Internet from entering your private LAN.
• Routers work at Layer 3 and route IP packets between networks.
• Routers are used to connect a LAN to a WAN (such as your small network to the Internet) but they can also be used to connect segments of a large LAN that has been subnetted into smaller segments.
• Routers route packets based on information in the IP routing table. You can see this table with the show ip route command on a Cisco router.
• Switches work at Layer 2 and switch Ethernet frames. Switches connect multiple devices on a local area network (LAN).
• Switches keep a table of Ethernet MAC addresses called a CAM Table or a Bridge forwarding table. You can see this table with the show mac-address-table command on a Cisco switch.
• Firewalls work at Layers 3 and 4 but some can also work at higher layers.
• Most firewalls can keep track of the states of TCP to prevent unwanted traffic from the Internet from entering your private LAN.
Network Engineer Job Interview - Questions & Answers
Network Engineer Interview - Questions & Answers
Question: Tell us something about Cisco PPDIOO Life-cycle approach?
ANS: PPDIOO stands for Prepare, Plan, Design, Implement, Operate, and
Optimize. The PPDIOO life-cycle approach is somewhat similar to the IT
Information Library (ITIL) framework in that both provide a network service’s
life-cycle framework to help ensure that when the project is implemented the
entire company will have everything it needs to operate and maintain the new
network. The Cisco PPDIOO model encompasses all steps, from network vision to
optimization. Figure 1-1 below is an illustration of the different phases of
the PPDIOO life-cycle approach.
Question: What are typical virus sources and how do you prevent virus
attacks?
ANS: Source of Computer virus:
Downloadable
Programs, Cracked Software, Email Attachments, Internet and Booting from CD
Preventing Virus attack: Install
quality antivirus, Install real-time anti-spyware protection, Keep anti-malware applications
current, Perform daily scans, Disable auto run, Disable image previews in
Outlook, Don't click on email links or attachments, Surf smart, Use a
hardware-based firewall and Deploy DNS protection
Question. What are some of the things you need to take into consideration
when planning an upgrade from one network operating system to another?
ANS. This is the mother of all planning activities because it will affect so many resources. The key here is testing and backups and that’s what the interviewer wants to hear. Other considerations include:
ANS. This is the mother of all planning activities because it will affect so many resources. The key here is testing and backups and that’s what the interviewer wants to hear. Other considerations include:
·
Network documentation
·
Ensuring that your hardware meets the minimum hardware
requirements for the new operating system
·
Creating a test network for testing the compatibility of
applications, hardware, and drivers with the new operating system
·
Gathering all updated drivers and patches/service packs required
for upgrade compatibility
·
Identifying workflow issues before converting
·
Separating workstation conversions from server conversions
·
Ensuring you have backups of data and the servers so that you
can revert back
Network addressing scheme
Q. How would you ensure that your servers are secure?
ANS. Security always begins at the physical level—it makes little difference that you’ve provided all the security the operating system and software can provide if someone can walk away with the box or the portable hard drive. The next step is to ensure you have the latest service packs for the operating system and applications running on the server.
ANS. Security always begins at the physical level—it makes little difference that you’ve provided all the security the operating system and software can provide if someone can walk away with the box or the portable hard drive. The next step is to ensure you have the latest service packs for the operating system and applications running on the server.
Question. A user contacts you and reports that their Windows 2000
workstation is having trouble connecting to the Web. You run the ipconfig command on the
computer and you find that the computer is not
referencing the correct primary DNS server. What must you do to remedy this?
ANS. Using this
question, the interviewer can assess your routing troubleshooting skills, an
essential part of network administration. In this case, you would want to check
the primary DNS setting in the IP configuration of the computer. If ipconfig
shows a setting for the default DNS server other than what you want, this means
the computer’s IP configuration is incorrect. Therefore, the Windows 2000
client computer needs to be reconfigured.
Question. What is
Service Level Agreement?
ANS: A service level agreement (SLA) is a contract between a
service provider (either internal or external) and the end user that defines
the level of service expected from the service provider. SLAs are output-based in that their purpose
is specifically to define what the customer will receive.
Question. Which
three commands can be used to check LAN connectivity problems on a router?
ANS:
1. show interfaces
2. show ip route
3. ping
Qustion What is SMTP & SNM?
ANS: SMTP: SMTP stands for Simple Mail Transfer Protocol.
It deals with the methods, to send and receive email from one client to another
over the internet. It has a wide breadth that covers the mail servers and the
applications that are used to send/receive emails. When you compose a mail and
send it, the SMTP client communicates with the mail server and verifies the
information about the email and the destination. Then the SMTP server sends
your mail to the destination, and their SMTP client handles the receiving
process in the same manner.
SNMP: SNMP stands for Simple Network Management
Protocol. As the name suggests, it manages various devices attached to a TCP /
IP network. There are three tiers in this protocol. The SNMP Manager, SNMP
Agent and the Managed Device. SNMP Manager is essentially a controller while
SNMP Agent acts as an interface between the devices and the network. The
Managed Device is the device that is controlled by the above two.
SNMP and SMTP are two standards that work together in harmony
to achieve two different tasks. They work in such a way that one can control
SMTP servers and MTAs through SNMP Managers. Further, SNMP Managers are capable
of sending alerts through SMTP mail servers.
Question. How does
Frame Relay Work?
ANS: Frame relay is a packet-switching telecommunication
service designed for cost-efficient data transmission for intermittent traffic
between local area networks (LANs) and between endpoints in wide area networks
(WANs).
Question. What is ATM technology?
ANS: ATM is a connection-oriented, unreliable (does not
acknowledge the receipt of cells sent), virtual circuit packet switching
technology. The cost of maintaining separate, specialized networks for
computer, voice, and video is high. To reduce networking costs, ATM enables
integration of all of these services on a single network and the combination of
existing networks into a single infrastructure. In particular, Windows
operating systems provide rich connectivity using Asynchronous Transfer Mode
(ATM) while maintaining support for legacy systems.
Question. How does the DSL work?
ANS: When you connect to the Internet, you might connect
through a regular modem, through a local-area network connection in your
office, through a cable modem or through a digital subscriber line (DSL)
connection. DSL is a very high-speed connection that uses the same wires as a
regular telephone line.
Question. Do you know about MPLS?
ANS: (MPLS is that it’s a technique, not a service) - Multiprotocol
Label Switching (MPLS) is a type of data-carrying technique for high-performance
telecommunications networks that directs data from one network node to the next
based on short path labels rather than long network addresses, avoiding complex
lookups in a routing table. MPLS operates at a layer that is generally
considered to lie between traditional definitions of OSI Layer 2 (data link
layer) and Layer 3 (network layer), and thus is often referred to as a layer
2.5 protocol.
Question. How does
MPLS work?
ANS: In MPLS, packets are directed through the network based
on an assigned label. The label is associated with a predetermined path through
the network, which allows a higher level of control than in packet-switched
networks. MPLS routing allow differing Qos characteristics and priorities to be
assigned to particular data flows, and operators can predetermine fallback
paths in the event that traffic must be rerouted.
Question. What is VRF?
ANS: Virtual routing and
forwarding (VRF) is a technology included in IP (Internet Protocol) network
routers that allows multiple instances of a routing table to exist in a router
and work simultaneously. This increases functionality by allowing network paths
to be segmented without using multiple devices. Because traffic is
automatically segregated, VRF also increases network security and can eliminate
the need for encryption and authentication. Internet service providers (ISPs)
often take advantage of VRF to create separate virtual private networks (VPNs)
for customers; thus the technology is also referred to as VPN routing and
forwarding.
Question. What is
MPLS VPN?
ANS: Multiprotocol Label
Switching (MPLS) is a standards-based technology used to speed up the delivery
of network packets over multiple protocols – such as the Internet Protocol
(IP), Asynchronous Transport Mode (ATM) and frame relay network protocols.
A virtual private network
(VPN) uses shared public telecom infrastructure, such as the Internet, to
provide secure access to remote offices and users in a cheaper way than an
owned or leased line. VPNs are secure because they use tunneling protocols and
procedures such as Layer Two Tunneling Protocol (L2TP)
Question. What is
difference between Route Distinguisher and Route Target.
ANS: The Route-Distinguisher (RD) & Route-Target (RT) are two
different concepts that are both used in an MPLS VPN. The RD is used to keep
all prefixes in the BGP table unique, and the RT is used to transfer routes
between VRF’s/VPNS.
Question. What is
VPLS
ANS: Virtual Private LAN Service (VPLS) is a way to provide
Ethernet-based multipoint to multipoint communication over IP or MPLS networks.
It allows geographically dispersed sites to share an Ethernet broadcast domain
by connecting sites through pseudo-wires. The term 'sites' includes
multiplicities of both servers and clients. The technologies that can be used
as pseudo-wire can be Ethernet over MPLS, L2TPv3 or even GRE. There are two
IETF standards track RFCs (RFC 4761 and RFC 4762) describing VPLS
establishment.
Mr.16x9 blog
Theme images by Jason Morrow. Powered by Blogger.